Data Security
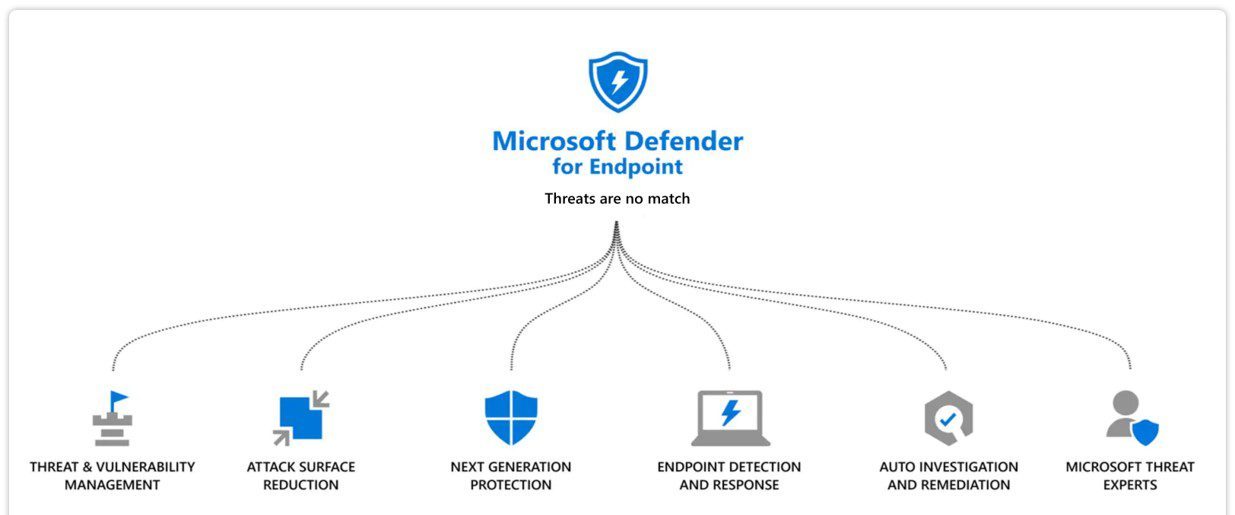
Microsoft Defender for Endpoint
[kc_row use_container=”yes” _id=”669468″ cols_gap=”{`kc-css`:{}}” force=”__empty__” css_custom=”{`kc-css`:{`any`:{`background`:{`background|`:`eyJjb2xvciI6InRyYW5zcGFyZW50IiwibGluZWFyR3JhZGllbnQiOlsiIl0sImltYWdlIjoibm9uZSIsInBvc2l0aW9uIjoiMCUgMCUiLCJzaXplIjoiYXV0byIsInJlcGVhdCI6InJlcGVhdCIsImF0dGFjaG1lbnQiOiJzY3JvbGwiLCJhZHZhbmNlZCI6MH0=`}}}}”][kc_column width=”12/12″ video_mute=”no” _id=”947356″][kc_column_text _id=”7959″]Microsoft Defender for Endpoint Security tools are continuing to become smarter,…
What is Microsoft Defender?
[kc_row use_container=”yes” _id=”95834″ cols_gap=”{`kc-css`:{}}” force=”__empty__” css_custom=”{`kc-css`:{`any`:{`background`:{`background|`:`eyJjb2xvciI6InRyYW5zcGFyZW50IiwibGluZWFyR3JhZGllbnQiOlsiIl0sImltYWdlIjoibm9uZSIsInBvc2l0aW9uIjoiMCUgMCUiLCJzaXplIjoiYXV0byIsInJlcGVhdCI6InJlcGVhdCIsImF0dGFjaG1lbnQiOiJzY3JvbGwiLCJhZHZhbmNlZCI6MH0=`}}}}”][kc_column width=”12/12″ video_mute=”no” _id=”716813″][kc_column_text _id=”111941″]What is Microsoft Defender and how can it help my business?…
Stress From Your RSS – The New Hack On The Block!
[kc_row use_container=”yes” force=”no” column_align=”middle” video_mute=”no” _id=”43009″][kc_column width=”12/12″ video_mute=”no” _id=”330935″][kc_column_text _id=”917220″]Important News! – We explain how hackers can take control of…
Cyber Security Terms and Definitions
[kc_row use_container=”yes” _id=”100608″][kc_column width=”12/12″ video_mute=”no” _id=”84932″][kc_column_text _id=”293616″]The nature of cyber-attacks has changed dramatically in recent years. Over this period, there…
The Covid and Cyber Threat Parallels
[kc_row use_container=”yes” force=”no” column_align=”middle” video_mute=”no” _id=”859766″][kc_column width=”12/12″ video_mute=”no” _id=”776134″][kc_column_text _id=”890201″]We’ve experienced a sobering introduction to 2021, with the news of…
Secure Score – the answer to cyber threats?
[kc_row use_container=”yes” force=”no” column_align=”middle” video_mute=”no” _id=”962119″][kc_column width=”12/12″ video_mute=”no” _id=”606371″][kc_column_text _id=”45967″] There is a strong possibility that lockdown may have changed…
Protect your personal data, or the public?
[kc_row use_container=”yes” force=”no” column_align=”middle” video_mute=”no” _id=”12288″][kc_column width=”12/12″ video_mute=”no” _id=”453984″][kc_column_text _id=”216915″] Author: Sam Nunn For years there have been massive debates around…