Data Security
What is Passwordless Authentication?
[kc_row use_container=”yes” _id=”606925″][kc_column width=”12/12″ video_mute=”no” _id=”528259″][kc_column_text _id=”760657″]Following on from our blog on Implementing Multi-Factor Authentication, here we will look at…
Windows Server 2012 End Of Life
[kc_row _id=”363794″][kc_column width=”12/12″ video_mute=”no” _id=”785820″][kc_column_text _id=”871753″]Windows Server 2012 End Of Life! Are you still using Windows Server 2012 or 2012…
Implementing Multi-Factor Authentication
[kc_row use_container=”yes” _id=”577358″][kc_column width=”12/12″ video_mute=”no” _id=”279052″][kc_column_text _id=”63655″]Implementing Multi-Factor Authentication (MFA) is a great way to improve the security of your…
Watch Out – The New Shared Mailbox Hack!
[kc_row use_container=”yes” _id=”739426″ cols_gap=”{`kc-css`:{}}” force=”__empty__” css_custom=”{`kc-css`:{`any`:{`background`:{`background|`:`eyJjb2xvciI6InRyYW5zcGFyZW50IiwibGluZWFyR3JhZGllbnQiOlsiIl0sImltYWdlIjoibm9uZSIsInBvc2l0aW9uIjoiMCUgMCUiLCJzaXplIjoiYXV0byIsInJlcGVhdCI6InJlcGVhdCIsImF0dGFjaG1lbnQiOiJzY3JvbGwiLCJhZHZhbmNlZCI6MH0=`}}}}”][kc_column width=”12/12″ video_mute=”no” _id=”957422″][kc_column_text _id=”240725″]This blog is aimed at the business owner and users, many…
The Newest Email Hack – How Credential Management Can Hinder Or Help Your Cyber Security
[kc_row use_container=”yes” _id=”528617″ cols_gap=”{`kc-css`:{}}” force=”__empty__” css_custom=”{`kc-css`:{`any`:{`background`:{`background|`:`eyJjb2xvciI6InRyYW5zcGFyZW50IiwibGluZWFyR3JhZGllbnQiOlsiIl0sImltYWdlIjoibm9uZSIsInBvc2l0aW9uIjoiMCUgMCUiLCJzaXplIjoiYXV0byIsInJlcGVhdCI6InJlcGVhdCIsImF0dGFjaG1lbnQiOiJzY3JvbGwiLCJhZHZhbmNlZCI6MH0=`}}}}”][kc_column width=”12/12″ video_mute=”no” _id=”784829″][kc_column_text _id=”866056″]Who are you sharing your mailbox with? This blog follows on…
Vissensa achieve the latest Cyber Essentials Plus certification!
[kc_row use_container=”yes” _id=”299630″][kc_column width=”12/12″ video_mute=”no” _id=”593570″][kc_column_text _id=”363115″]This is the biggest update to Cyber Essentials technical controls since its launch. These…
Cyber Essentials Certification – Is it Relevant To SME’s?
[kc_row use_container=”yes” _id=”489673″][kc_column width=”12/12″ video_mute=”no” _id=”235807″][kc_column_text _id=”699694″]Complacency in Cyber Security still runs high The Covid-19 pandemic has clearly given cybercriminals…
Microsoft Defender for Identity
[kc_row use_container=”yes” _id=”928651″ cols_gap=”{`kc-css`:{}}” force=”__empty__” css_custom=”{`kc-css`:{`any`:{`background`:{`background|`:`eyJjb2xvciI6InRyYW5zcGFyZW50IiwibGluZWFyR3JhZGllbnQiOlsiIl0sImltYWdlIjoibm9uZSIsInBvc2l0aW9uIjoiMCUgMCUiLCJzaXplIjoiYXV0byIsInJlcGVhdCI6InJlcGVhdCIsImF0dGFjaG1lbnQiOiJzY3JvbGwiLCJhZHZhbmNlZCI6MH0=`}}}}”][kc_column width=”12/12″ video_mute=”no” _id=”699433″][kc_column_text _id=”245535″]Microsoft Defender for Identity Security tools are continuing to become smarter…
Microsoft Defender for Cloud Apps
[kc_row use_container=”yes” _id=”312891″ cols_gap=”{`kc-css`:{}}” force=”__empty__” css_custom=”{`kc-css`:{`any`:{`background`:{`background|`:`eyJjb2xvciI6InRyYW5zcGFyZW50IiwibGluZWFyR3JhZGllbnQiOlsiIl0sImltYWdlIjoibm9uZSIsInBvc2l0aW9uIjoiMCUgMCUiLCJzaXplIjoiYXV0byIsInJlcGVhdCI6InJlcGVhdCIsImF0dGFjaG1lbnQiOiJzY3JvbGwiLCJhZHZhbmNlZCI6MH0=`}}}}”][kc_column width=”12/12″ video_mute=”no” _id=”561655″][kc_column_text _id=”366629″]Microsoft Defender for Cloud Apps Security tools are continuing to become…
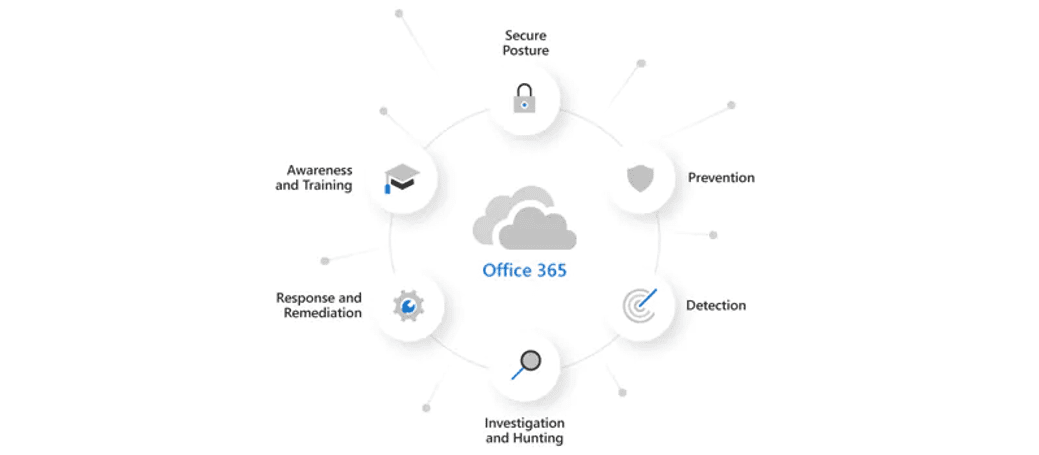
Microsoft Defender for Office 365
[kc_row use_container=”yes” _id=”629969″ cols_gap=”{`kc-css`:{}}” force=”__empty__” css_custom=”{`kc-css`:{`any`:{`background`:{`background|`:`eyJjb2xvciI6InRyYW5zcGFyZW50IiwibGluZWFyR3JhZGllbnQiOlsiIl0sImltYWdlIjoibm9uZSIsInBvc2l0aW9uIjoiMCUgMCUiLCJzaXplIjoiYXV0byIsInJlcGVhdCI6InJlcGVhdCIsImF0dGFjaG1lbnQiOiJzY3JvbGwiLCJhZHZhbmNlZCI6MH0=`}}}}”][kc_column width=”12/12″ video_mute=”no” _id=”82781″][kc_column_text _id=”670″]Microsoft Defender for Office 365 Microsoft Defender for Office 365 should…